Presentation - Security
Information Security


Information Security
Question: What makes a system insecure?
Answer: Switching it on.
"The only system which is truly secure is one which is switched off and unplugged, locked in a titanium lined safe, buried in a concrete bunker, and is surrounded by nerve gas and very highly paid armed guards. Even then, I wouldn't stake my life on it."
- Gene Spafford of Purdue University

Security problems manifest themselves in four main ways:
- Physical Security Holes
- Software Security Holes
- Incompatible Usage Security Holes
- A weak and inconsistent security philosophy

Physical Security Holes.
These can be caused by giving unauthorized persons physical access to the machine, where this might allow them to perform things that they shouldn't be able to do.
Example 1
Problem:
The SPARC workstation room is has no restrictions as to who may sit down and use one of the machines. If a person can reboot the machine into a single-user mode, they may be able to get direct access to workstation files.
Solution:
Lock terminal rooms and use something such a key-lock or swipe-card physical security system on the doors. For example, the SGI lab on the Main floor of Math Sciences.
Example 2
Problem:
A company makes backup tapes of confidential files. Although network permissions are secure, anyone who has access to the backup tapes can view the information they contain.
Solution:
Physically lock any backup storage so that only a small number of trusted people have access.

Software Security Holes
Most often cause by bugs in security systems. Poorly written items of "privileged"
software are the most common bugs.
Example:
A user gets access to a intermediate level daemon account. A bug in the system allows them to change their file access to read/write for all files on the system.
Solutions to Software Holes:
Try to structure your system so that as little software as possible runs with high-level privileges. Choose Software that you know to be well-tested and robust. These solutions are not perfect, but will decrease the possibility of software holes.

Incompatible Usage Security Holes
A combination of hardware and software exists which, when used as a system is seriously flawed from a security point of view. It is the incompatibility of trying to do two unconnected but useful things which creates the security hole.
Example:
A computer requires a physical security key in the serial port in order for the user to access confidential files. The user has a peripheral that runs at interrupt level X. By coincidence, the software for the security key also runs at interrupt level X, and nullifies the security key's requirement.
Solutions for Incompatible Usage Security Holes:
It is extremely difficult to find this kind of hole if it exists. The best way to avoid this type of hole is to test security regularly and try to maintain a standard for purchasing hardware and software.

A Weak and Inconsistent security philosophy
Problem:
The fourth kind of security problem is one of perception and understanding. Perfect software, protected hardware, and compatible components don't work unless you have selected an appropriate security policy and turned on the parts of your system that enforce it.
Solutions:
Security is relative to a set of policies and the operation of a system in conformance with that policy. It is important that system administrators are well aware of policies implemented for security. They must follow them to the letter to ensure a consistent and reliable system of security.

Passwords
Why are passwords so important?
Because they are the first line of defense against interactive attacks on a system. It can be stated simply: if a cracker cannot interact with your system, and he has no access to read or write the information contained in the password file, then he has almost no avenues of attack left open to break your system.

How should passwords be created?
The only way to get a reasonable amount of variety in your passwords is to make them up.
DO NOT:
- modify any part of your name or name+initials
- modify a dictionary word
- Use known acronyms unless they are very unusual.
- any systematic, well-adhered-to algorithm whatsoever
NEVER use passwords like:
alec7 - based on users name and too short)
gillian - girlfriends name (in a name dictionary)
nailing - girlfriends name backwards (easily derived from gillian)
porche911 - in a dictionary
12345678 - People can watch you type it easily
Computer - just because it's capitalized doesn't make it safe
merde - in a French dictionary
mr.spock - it's in a sci-fi dictionary
zeolite - it's in a geological dictionary

Important:
ANY password derived from ANY dictionary word (or personal information), constitutes a potentially guessable password.
Examples of less guessable passwords:
qA98gW2n
- fairly random, no patterns, not found in any dictionary. (Unfortunately, hard to remember)
A good method of maintaining a pseudo-random look to passwords while making them a little easier to remember is to use a combination of short acronyms and/or numbers. You don't want to have to write them down, since that immediately compromises the security of your account.
Good Password example:
ms28JKfd
- ms - The darkest and dingiest building on campus - math sciences
- 28 - The number of whiskey shots it takes to put you under the table - 28
- JK - The (capitalized) initials of your favorite star trek character - James Kirk
- fd - The marks of your first two tries at Math 251 - F and D

Password Security: A Case Study
This case study shows how few passwords are "Hard-to-guess".
Remember, a Hacker only needs one valid password to gain a toe-hold on a system
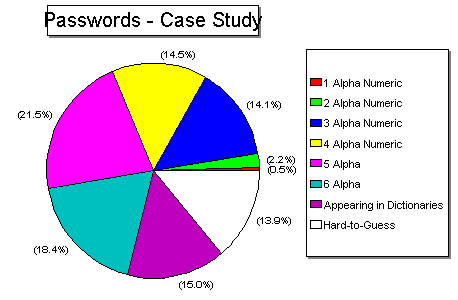

Why you should never use the same password on two systems.
You can never REALLY trust your system administrator. Tomorrow they could be logging into another account of yours because you used the same password. This is doubly important when using everyday BBS's and other connections where you don't know the administrators that well.

One-Time Password Technology
One-time passwords are generated each time you need to get into a system. By using a different password each time, hackers can not make head-way by making repeated guesses on a password. Since it changes each time, the odds never improve for the Hacker as they make more guesses.
There are two ways to generate them:
Generation Method:
- The user has a mini card-computer that generates a password depending on the time.
- The user types in the password to the system.
- The system generates the password, also depending on the time, and compares to the one the user typed in.
Problems:
- If the system time or the user time is wrong, the user can not get into the system.
Challenge Number Method:
- User sends user name to system.
- Systems sends the user a "Challenge" number.
- User uses the Challenge number to generate password
- User sends password to the system
- System verifies the password according to the challenge number.

Who tries to break Security Systems?
Answer: Hackers & Crackers
Definitions of Hackers/Crackers:
From a Sys Admin Point of View:
Cracker
Someone who gets their kicks from breaking into systems. Crackers often have no justification for this, except "because it's possible". Often times, crackers have vandalistic streaks and wreak havoc by deleting files or crashing machines.
They are generally considered mischievous and annoying, but of no real threat to sensitive information.
Hacker
Someone who is a really good Cracker. Hackers have been given grudging respect by the security community simply because they are very good at what they do. They are also considered more dangerous, and often to have motives other than "just having fun".
Definitions of Hackers/Crackers:
From a Hacker/Cracker Point of View:
Hacker
A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary.
Cracker
An individual who attempts to gain authorized access a computer system. These individuals are often malicious and have many means at their disposal for breaking into a system. The term was coined in 1985 by hackers in defense against journalistic misuse of "hacker".

History of Hackers and Crackers
1878
First teenage males flung off phone system by enraged authorities over fraudulent use.
1971
First Phone Phreaks start a Hacker magazine.
1978
First personal computer bulletin board system created.
1989
Florida probation office crossed with phone-sex line in switching-station stunt.
1990
Marks the start of a series of arrests, by the US Secret Service, in the Hacker/Cracker community that lasts several years. This is commonly known as the "Hacker Crackdown"

Hacker Ethic
- Access to computers should be unlimited and total.
- All information should be free.
- Mistrust authority -- promote decentralization.
- Hackers should be judged by their hacking.
Defined by Stephen Levy, author of "Hackers - Heroes of the Computer Revolution"

Hacker/Cracker/Sys Admin Tools
There are a variety of tools out there that can be used by either group:
- Hackers/Crackers can use to help them break into systems.
- System Administrators to help create good passwords and a more secure system.

Examples of Hacker/Security tools
COPS by Dan Farmer (UNIX)
- an extensive security testing system
- rudimentary password cracker
- routines to check the filestore for suspicious changes
- routines to check permissions of essential system and user files
- checks to see whether any system software behaves in a way which could cause problems
Crack by Alec Muffett
- Crack is a program written with one purpose in mind: to break insecure passwords.
- efficient and friendly
- publicly available
- lets user specify how to form the words to use as guesses at users passwords
- networking capability, allowing the load to be spread out

Examples of Hacker/Security tools - Sniffers
Sniffers capture the information going over the network.
Example:
- User types name and password in
- Computer sends packet with name, password, and destination machine enclosed.
- Destination machine accepts, all other machines ignore.
- Sniffer programs put a machine in to "promiscuous" mode which accepts all packets.
- Information is then stores and decryption routines can be run later.


Topics:
[
Information Security
|
Passwords
|
Hackers
|
Security Tools
|
Firewalls
|
Data Encryption
|
Viruses
|
Piracy
|
HOME
]

References:
- Potpourri of Security Info - US Navy
- Network/Computer Security Technology - Frequently Asked Questions
- Frequently Asked Questions (FAQ)
- Security FAQs
- The New Hacker's Dictionary - Table of Contents
- excite NetDirectory: General/Computing/Security_And_Encryption/
Cracking Tools:
Crack v4.1f and UFC are available from: ftp.uu.net (137.39.1.9)
In the directory: /usenet/comp.sources.misc/volume28
As: crack/part01.Z to part05.Z ( 5 files )
And ufc-crypt/part01.Z & part02.Z ( 2 files )
A UNIX password cracker for the Thinking Machine CM/2 and CM/200 Connection Machines is available for FTP from
ftp.denet.dk:/pub/misc/cm200-UFC.tar.Z
Knock yourself out!

























