Abstract
This article is a preliminary survey of some methods, techniques and tools aimed at managing corporate knowledge from a corporate memory (CM) designer's perspective. In particular, it analyzes problems and solutions related to the following steps: detection of needs of CM, construction of the CM, its diffusion (specially using the Internet technologies), its use, its evaluation and its evolution.
1.1 Corporate Memory: Definitions
The objectives of knowledge management (KM) in an organization are to promote knowledge growth, knowledge communication and knowledge preservation in the organization (Steels, 93). Knowledge management is a very complex problem and can be tackled from several viewpoints: socio-organizational, financial and economical, technical, human, and legal (Barthès, 1996).
There is an increasing industrial interest in the capitalization of knowledge (i.e. both theoretical knowledge and practical know-how) of groups of people in an organization, such groups being possibly dispersed geographically. In (Van Heijst, Van der Spek, and Kruizinga, 1996) «corporate memory» is defined as an «explicit, disembodied, persistent representation of knowledge and information in an organization». For example, it may include knowledge on products, production processes, clients, marketing strategies, financial results, plans and strategical goals, etc. (Nagendra Prasad and Plaza, 1996) define corporate memory as «the collective data and knowledge resources of a company including project experiences, problem solving expertise, design rationale, etc»: it may include databases, electronic documents, reports, product requirements, design rationale, etc. It is a «repository of knowledge and know-how of a set of individuals working in a particular firm» (Euzenat, 1996) and its building relies on the «will to preserve, in order to reuse them later or the most rapidly, reasonings, behaviours, knowledge even in their contradictions and with all their variety»(Pomian, 1996). Knowledge capitalization is the process which allows to reuse, in a relevant way, the knowledge of a given domain, previously stored and modelled, in order to perform new tasks (Simon, 1996). The purpose is to «locate and make visible the enterprise knowledge, be able to keep it, access it and actualize it, know-how to diffuse it and better use it, put it in synergy and valorize it»(Grundstein, 1995).
Several kinds of knowledge can be found in a company: explicit or tacit knowledge (Nonaka, 1991). Therefore, in any operation of knowledge capitalization, it is important to identify crucial knowledge to be capitalized (Grundstein and Barthès, 1996). It has an influence on the kind of CM needed by the enterprise. This CM should help to support the integration of resources and know-how in the enterprise and the cooperation by effective communication and active documentation (Durstewitz, 1994).
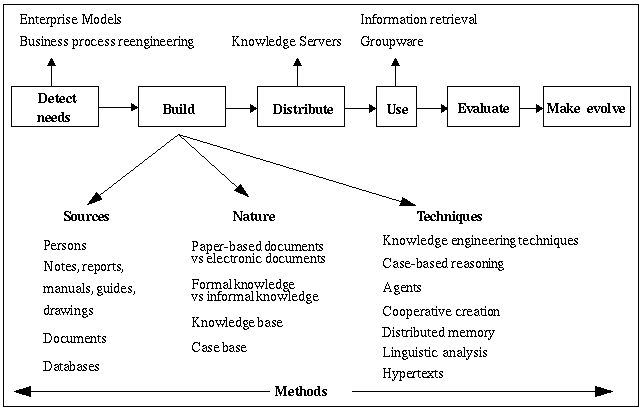
As noticed in (Nonaka, 1991; Van Engers, Mathies, Leget and Dekker, 1995), the knowledge chain consists of seven links: listing the existing knowledge, determining the required knowledge, developing new knowledge, allocating new and existing knowledge, applying knowledge, maintaining knowledge, disposing of knowledge. So, we can consider the building of the CM as relying on the following steps (summed up in Figure 1): (1) Detection of needs in corporate memory, (2) Construction of the corporate memory, (3) Diffusion of the corporate memory, (4) Use of the corporate memory, (5) Evaluation of the corporate memory, (6)Maintenance and evolution of the corporate memory.

For each step, we will analyse some methodological or technical proposals offered by researchers. Let us notice that several kinds of publications can be found: survey on KM, analysis of types of knowledge available in a company, reports of industrial experiments, proposal of a general architecture for CM, thorough study of a particular technique such as some knowledge-processing techniques stemming from artificial intelligence (AI) and used here for solving a peculiar problem underlying computational CM building. The variety of research topics possibly involved in CM management is illustrated by Figure 1. Clearly, this complex problem has at least organizational aspects to be tackled, and technical aspects to be solved. According to (Kühn and Abecker, 1997) , computer scientists concerned by the use of Information and Communication Technology for KM support tend to ignore the specific requirements and constraints for successful knowledge management in industrial practice while specialists in KM often treat only roughly the aspects of computer support. Therefore, building a CM requires a multidisciplinary approach.
1.2 Corporate Memory Industrial Needs
An enterprise is not only a unit of production of goods or services conform to the expectations of clients, in the best conditions of cost, deadline and quality, but it is also a knowledge production unit (Grundstein, 1995). The nature of the needed CM and the efforts needed for building it may depend on the size of the company (cf. wide-sized groups vs small-sized and medium-sized firms). The motivations can be various: (a) to avoid loss of know-how of a specialist after his retirement or mutation, (b) to exploit the experience acquired from past projects, and to keep some lessons from past, in order to avoid to reproduce some mistakes, (c) to exploit the knowledge map of the company for the corporate strategy: a regular inventory of the firm know- how should improve the enterprise ability to react and adapt to change, (d) to improve information circulation and communication in the enterprise, (e) to improve learning of employees in the enterprise (new as old employees), (f) to integrate the different know-how of an organization.
1.3 Knowledge in the Enterprise
Several typologies of knowledge in the enterprise were proposed in literature.
They can be useful to determine the essential knowledge the compagny needs
to capitalize (Durstewitz, 1994). (Grundstein,
1995; Grundstein and Barthès,
1996) distinguish on the one hand, know-how (ability to design,
build, sell and support products and services) and on the other hand, individual
and collective skills (ability to act, adapt and evolve). In a company,
there are tangible elements (data, procedures, plans, models, algorithms,
documents of analysis and synthesis) and intangible elements (abilities,
professional knacks, private knowledge, knowledge of company history and
of decisional contexts...). Therefore, in a capitalization operation, tangible
elements can be taken into account through KM (technical data management,
document management, configuration management), while intangible elements
require know-how formalization (acquisition and representation of know-how
and reasoning on such know-how). Know-how, technical facts, product requirements,
design rationale, experience or expertise are examples of knowledge types
useful for corporate memory (Durstewitz, 1994).
More specifically in the framework of manufacturing industry, several
categories of industrial knowledge useful for design activity are proposed
in (Bourne, 1997) (see
below).
1.4 Typologies of Corporate Memories
The memory of an enterprise includes not only a «technical memory» obtained by capitalization of its employees' know-how but also an «organizational memory» (or «managerial memory») related to the past and present organizational structures of the enterprise (human resources, management, etc.) and «project memories» for capitalizing lessons and experience from given projects (Pomian, 1996). (Tourtier, 1995) distinguishes: (a) profession memory, composed of the referential, documents, tools, methods used in a given profession, (b) company memory related to organization, activities, products, participants (e.g. customers, suppliers, sub-contractors), (c) individual memory characterized by status, competencies, know-how, activities of a given member of the enterprise, (d) project memory comprising the project definition, activities, history and results. (Grundstein and Barthès, 1996) distinguish company technical knowledge (i.e. used everyday inside the company, its business units, departments, subsidiaries by the employees for performing their daily job) from strategic corporate knowledge used by the company managers.
The paper will successively analyse problems and solutions linked to detection of needs, construction of the CM, its diffusion, use, evaluation and maintenance. Then we will give several examples of dedicated methods and we will summarize the lessons of this study.
2.1 Detection of Needs of Corporate Memory
As successful information system development in general, successful CM development must be "underpinned by a clear focus on the situations of use and the needs of users" (Thomas, 1996), i.e. on the human issues of the development. The history of systems development "shows repeatedly that it is the human issues which "make or break" new methods and tools at work" (Buckingham Shum, 1997). So detecting the "right" users' needs, or the "right" CM needed, is the first task of the CM designers.
Detecting the "right" needs is not a simple task. CM designers have to learn as much as possible about who users are, which tasks they have to perform, in which situations, which knowledge types they need to memorize and retrieve (for achieving the tasks), which tools they use, etc. So doing, CM designers have to face with problems about users, tasks, situations, etc. Examples of such problems are:
Here are some of the solutions currently adopted to detect CM needs.
2.1.2.1 Underlying Approach: ``Stakeholder-Centered Design''
The approach to needs detection cannot be disconnected from the approach to the overall development of the CM, or underlying approach. The main underlying approach is the so-called User-Centered Design (UCD), or Human-Centered Design (HCD), approach. The reason for using a UC[H]D approach is "to ensure that the memory is defined in terms of users' needs" (Durstewitz, 1994). The related UC[H]D methods "cover requirements determination, design and implementation, and are concerned with the social as well as technical issues in new system development [...]. The philosophy underpinning this approach is that effective systems are created by a partnership between developers and the users and/or stakeholders in the organisation which is to operate the new system." (Eason and Olphert, 1996). The term "stakeholders" is worth discussing here. This term refers to "any individual within the community where the system may be implemented who has an interest or "stake" which may be affected by the system"(Eason and Olphert, 1996); it refers to "anyone who stands to gain from it [the system], and anyone who stands to lose" (Macaulay, 1996). Stakeholders include "potential users but are not restricted to them; other stakeholders may be purchasers, customers, maintainers, etc. "(Eason and Olphert, 1996). The current trend among CM developers is to consider stakeholders rather than users (strictly speaking). So CM design/development could be called Stakeholder-Centered Design/Development. As (Eason and Olphert, 1996) claimed: "Systems development should be a partnership in which developers contribute an understanding of the technical opportunities and the methods of design, and the stakeholders contribute their expertise about the domain of application and existing organisational practices and have a right to judge what is in their best interests as the potential owners of the future that is being constructed."
2.1.2.2 Approaches to Requirements Analysis
Approaches to needs detection can be appropriately described in terms of requirements analysis, because (1) getting at the users' needs is the aim of requirements analysis (Thomas, 1996), and (2) research on CM and KM often refers to requirements analysis (e.g., Kühn and Abecker, 1997). "The earlier designers of systems understand the needs and problems of their users, and [...] the better they understand them then the more able they will be to develop systems which meet users' needs", according to (Macaulay, 1996), that describes four types of approaches to CSCW requirements analysis (cf. a great amount of CSCW work is done in the context of CM (Wærn, 1996)):
Traditional Approaches. Traditional approaches are approaches such as the structured analysis approach, or the object-oriented approach (cf. OO Analysis). In such approaches users have a passive role; they are considered as the sources of information and the reviewers of models developed, and the systems analyst is considered as responsible for eliciting requirements from users.
Participation. In the Participation approach, "users are expected to contribute", by assisting in analysing their problems at work, complete job satisfaction questionnaires, etc. Participation is used "in situations in which initiators of projects do not have all the information needed to design the change, and where users have considerable power to resist".
Design Team. The formation of a design team is often recommended "to smooth the transition from requirements to design". In the design team, the roles of the technical experts and the customers are clearly identified. Technical experts "contribute their skills to the creation of a system", and customers "are concerned with the world they will have to inhabit after the change caused by the system".
Group Sessions. In the Group Sessions approach, people "jointly design systems in facilitated group sessions". Macaulay's cooperative requirements capture (Macaulay, 1996) is a stakeholder-centered approach consisting of the following steps: (1) identify the problem; (2) formulate the team; (3) group session 1: explore the user environment; (4) validate with users; (5) group session 2: identify the scope of the proposed system; (6) validate with stakeholders. Each group session has a number of steps; for example, session 1 includes: (a) the business case, (b) workgroups, (c) users, (d) tasks, (e) objects, (f) interactions, (g) consolidation. Each step includes an introduction, brainstorming, prioritisation and generation of agreed descriptions using checklists and proformas which deal with user related issues.
It is important to notice that requirements analysis is strongly related to evaluation: if for requirements analysis the aim is "to get at users' needs", for evaluation the aim is "to tune the system to make sure that it really does meet those needs" (Thomas, 1996).
Literature Review. Analysing the literature on CM is one of the classical methods used to detect CM needs. For example, from the Macintosh's (1997) work on knowledge asset management, Kühn and Abecker (1997) elicited the following "major impediments to more productivity in knowledge-based work process": (a) Highly-paid workers spend much of their time looking for needed information; (b) Essential know-how is available only in the heads of a few employees; (c) Valuable information is buried in piles of documents and data; (d) Costly errors are repeated due to disregard of previous experiences; (e) Delays and suboptimal product quality result from insufficient flow of information. These impedements can be considered as introducers to requirements.
Interviews/Discussions. Performing interviews or discussions is another classical method used for identifying CM needs. For example, Kühn and Abecker (1997) had interviews with prospective users and discussions with IT personnel and managers to get requirements. They suggest crucial requirements for the success of a CM information system project in an industrial practice: (a) Collection and systematic organization of information from various sources; (b) Integration into existing work environment; (c) Minimization of up-front knowledge engineering; (d) Active presentation of relevant information; (e) Exploiting user feedback for maintenance and evolution.
Observations/Experiments. Observing real CM practices or conducting experiments about them, are a third classical method used to detect CM needs. For example, observing the Design Rationale activity of a real industrial project conducted in a design office of Aerospatiale, the French aerospace company, Karsenty (1996) showed that designers having to reuse a past solution elaborated by others, often asked themselves: "Why did they do so and not else?" . If they had no answer to this question, experienced designers often considered the alternative solution they spontaneously found as better than the past one (even if the later revealed itself worse). Less experienced designers often selected the past solution. These results suggest requirements such as: a CM for Aerospatiale designers should contain justification or argumentation knowledge; this knowledge must be "past-solution oriented" for experienced designers, and "present-solution oriented" for less experienced designers.
2.1.2.4 Dedicated Methods and Approaches: Some Trends
Lead User Methodology. The "lead user methodology" (Urban and von Hippel , 1988) prescribes to perform needs detection with "lead users". Lead users are "users whose present strong needs will become general in a marketplace months or years in the future".
Advisibility Analysis. The CORPUS project (Grundstein and Barthès, 1996) offers a process-centered and problem-oriented approach called Advisibility Analysis for knowledge capitalization. The purpose is to help to determine the nature and field of crucial knowledge that needs to be capitalized, the company members who have this knowledge, in which form, the members who use this knowledge, when and how, and the risks in case no capitalization operation is performed. The main steps of this approach are: (1) Determine sensitive processes essential for the company functioning; (2) Distinguish determining problems that fragilize critical activities (i.e. activities contributing to sensitive processes); (3) Determine crucial knowledge necessary to solve determining problems.
Enterprise Models. Some research focus on enterprise analysis
and modelling (Fox, 1993) [http://www.aiai.ed.ac.uk/~entprise/enterprise/]
and can be useful during a CM construction. For example, the evolution
of the enterprise through time, its experience acquired from past projects
are elements interesting to take into account. An enterprise ontology,
defining concepts relevant for description of an enterprise, is proposed
in (Uschold, King, Moralee, and Zorgios,
1996). Such an ontology can be used as support for exchange of information
and knowledge in the enterprise (Fraser,
1994). Organizational structure, processes, strategies, resources,
goals, constraints and environment of the enterprise can thus be modelled.
Intra-enterprise modelling and inter-enterprises modelling can be distinguished.
(Beauchène, Mahé and Rieu,
1996) models an enterprise organization, using a model stemming from
quality management and focusing on "customer-supplier" relationships between
the enterprise members. The interest of exploiting an enterprise
model is to determine the weak points of the enterprise, that could possibly
be improved by a knowledge capitalization operation.
The MNEMOS EUREKA project (see http://www.delab.sintef.no/MNEMOS/dir.html)
aimed "to develop a new generation of information systems to increase the
competitivity of the enterprise through a better circulation of the corporate
knowledge, a more efficient management and support to the human creativity
processes". This project proposes an enterprise model based on eight
dimensions: document, programme, budget, contacts, organization,
material, calendar, results (Feray and Villefranche,
1997).
Cognitive Models. Theoretical models of workers' cognitive functioning and of knowledge used in work situations may be useful for needs detection purposes. (Bollon, 1997) showed the interest of these models and especially the methodological precautions they induce during field observations conducted to capitalize knowledge. (See also Poitou, 1997.)
Anthropotechnology. Anthropotechnology (Wisner, 1997) refers to the transfer of organisational systems and technologies in countries having different cultures. This methodology can be applied to design within the same country or the same organisation, in which different-culture subgroups can be identified. From the anthropology viewpoint, culture-related requirements need to be identified for a successful transfer.
Knowledge Networking. From the point of view of expertise sharing between CM developers, a project which anticipates what would happen in the future of CM development practice is CERES-GKN [http://www.cerc.wvu.edu/ceres/CERESGKN_brochure.html]. The goal of this project is to construct "a global knowledge network to enable environmentally sound product and process development". CERES-GKN "will identify consumer and producer requirements and needs for an environment-oriented infrastructure and product and process application". CERES-GKN "will develop a global network of knowledge bases (both proprietary and public domain) containing a variety of knowledge -- such as best practices, case studies, and expert advisory systems -- useful for designing products and processes that are at once environmentally sound, technologically feasible, and economically justifiable".
2.1.3 Conclusion
The phase of needs detection may help to determine the type of CM needed
(e.g. project memory, profession memory, organizational memory, individual
memory), the potential users of the CM, and the possible modes of exploitation
useful and adapted to their work environment.
2.2 Construction of the Corporate Memory
As emphasized during KAW'96 track on «Corporate Memory and Enterprise Modelling», a corporate memory is of course different from a knowledge-based system. The techniques adopted to build a CM depend on the available sources: human specialists, existing paper-based or electronic documents such as reports or technical documentation, E-mails, existing databases, case libraries, dictionaries, CAD drawings... They also depend on the nature of the needed CM according to the intended users: it may consist of paper-based documents making explicit the enterprise adequate members' knowledge, that had never been yet elicited and modelled (Dieng, Giboin, Amergé, Corby, Després, Alpay, Labidi, Lapalut, 1996) . It may also be a computational memory materialized through an intelligent documentary system, a knowledge base, a case-based system, a Web-based system or a multi-agent system. We note that even though paper-based or electronic documents can themselves represent a CM they are often considered as a first step in the implementation of the CM (Simon,1996).
In the next sections, we describe different approaches for the construction of a CM.
2.2.1 Non computational Corporate Memory
A non computational memory is made of paper-based documents on knowledge that had never been elicited previously. The construction of such a memory may be guided by two different aims: (a) to elaborate synthesis documents on knowledge that is not explicit in reports or technical documentation, and is more related to the know-how of the experts of the enterprise, (b) to improve enterprise production through expert propositions on their tasks in a design process.
In the first aim, the memory is composed of knowledge described in existing documents and interviews of experts, or elaborated from observations of experts' activity. The KADE-TECH Company proposes a method called CYGMA (Bourne, 1997) to produce different documents that contain memory about a profession (see below). (Simon, 1996) considers that this kind of memory provides «a global view of the knowledge of the firm», and «allows experts from different sites to describe their knowledge in the same format in order to be able, afterwards, to compare them more easily». But in (Simon, 1996), this elaboration of synthesis documents is a first step in the construction of the computational CM that it helps to implement: It enables homogeneization of know-how in different sites of an enterprise distributed geographically.
In the second aim, the firm RENAULT proposes MEREX approach (Corbel, 1997). This approach, guided by the Quality approach, is based on positive and negative experience return on previous projects. The memory is constituted by forms, where an expert can describe a solution or a decision in a task of design process. Those forms are validated by a system of check-list and stored in a form management system. They are used in the product specification phase, before the artefact design.
Remark: Notice that often such paper-based documents are put later in an electronic form, but we make a difference between simple electronic documents and an actual documentary system.
2.2.2 Document-based Corporate Memory
A document-based CM relies on the principle that all existing documents of the firm can constitute the CM. But those documents are not well-indexed or they constitute a personal bibliography for each expert of the firm. So the construction of such a CM begins by indexing all reports, synthesis documents or references used by the different experts. It requires an interface to manage documents (addition of documents, retrieval of documents...). (Poitou, 1995) considers that: «a good documentation system is very likely the least expensive and the most feasible solution to knowledge management» and prefers a computer assistant to documentation (i.e. to writing or reading) rather than knowledge representation: according to him, a document is already a representation of knowledge. So the main need is assistance in preparing, storing, retrieving and processing documents. The notion of corporate knowledge collective management system (Poitou, 1997) answers well to this need: e.g. SG2C proposed by Poitou and DIADEME proposed by Electricité de France (Ballay and Poitou, 1996; Ballay, 1997).
2.2.3 Knowledge-based
Corporate Memory
Knowledge engineering is naturally useful for building a CM based on
elicitation and explicit modelling of knowledge from experts
or even for a formal representation of knowledge underlying a document.
Therefore several researchers that have been working on expert systems
for years evolved towards CM building where they could exploit their past
experiences. However, the goal of a CM building is less ambitious
than an expert system: instead of aiming at an automatic solution for a
task (with automatic reasoning capabilities), a CM rather needs to be an
assistant to the user, supplying him/her with relevant corporate information
but leaving him/her the responsibility of a contextual interpretation and
evaluation of this information (Kuhn and Abecker, 1997).
(Kuhn and Abecker, 1997) notices that "in contrast
to expert systems, the goal of a CM is not the support of a particular
task, but the better exploitation of the essential corporate resource:
knowledge" but, however, cites some knowledge-based CM implemented
through an expert system (e.g. KONUS system aimed at support to crankshaft
design).
Knowledge engineering methods such as COMMET and CommonKADS can be useful in the construction of a CM, because they allow to analyse and represent an activity on the knowledge level. (Steels,1993) notices that the organization of a production is more and more horizontal, i.e. the production is organized through activities gathering experts stemming from different departments. So the CM of such an enterprise can be based on activity description through three perspectives: task, method and information and can thus be realized using KREST. By the same way, even though CommonKADS was not primarily dedicated to CM building, some models offered by CommonKADS (organization, task, agent, communication and expertise models) give an interesting basis for knowledge-based CM (Kingston, 1994; VanderSpek, 1994; Corby and Dieng, 1997).
2.2.4 Case-based Corporate Memories
The exploitation of another AI technique, case-based reasoning, can also be very useful (Simon and Grandbastien, 1995; Simon, 1996). Indeed each firm has a collection of past experiences (successes or failures) that can be represented explicitly in a same representation formalism allowing to compare them. The use of a case base for representing the CM is dedicated for the following aims: (1) avoid the scattering of the expertise by concentrating knowledge of all experts in dedicated cases, (2) allow a continuous evolution of the CM thanks to the progressive addition of new cases.
Case-based reasoning allows to reason from experiences and cases already
encountered, in order to solve new problems: e.g. for maintenance of a
complex equipment, the collective memory of past incidents can be useful
for taking a decision in case of a new breakdown. The retrieval of a similar
past case can be used to suggest a solution to a new problem to be solved
(this solution can be reused or adapted if needs be). Improving representation
of the cases, organization and indexing of the case base is important for
enhancing efficiency of case retrieval.
In (Simon, 1996 ; Simon,
1997), the author describes an example
in metallurgy, where the aim was to capitalize knowledge and know-how about
descriptions of production of produced steels and metallurgical defects
encountered during these productions. The purpose of the CM was to exploit
past successes and failures in order to minimize error risks in design
of new steels. The method consisted of: (1) creating synthesis documents
common to all sites and respecting an homogeneous format, (2) proposing
models to implement a CM based on such synthesis documents, (3) providing
capitalization processes allowing to use the CM for defects detection purpose.
2.2.5 Construction of a Distributed Corporate Memory
A distributed CM is interesting for supporting collaboration and knowledge sharing between several groups of people in an organization or in several collaborating organizations, such groups being possibly dispersed geographically. A distributed memory is essential for virtual enterprises made of distributed organizations and teams of people that meet and work together online. Generally, for such virtual enterprises, this distributed memory naturally relies on the exploitation of the Internet and of the Web (O'Leary, 1997). For example, the GNOSIS project on intelligent manufacturing (Gaines, Norrie, Lapsley and Shaw, 1996) involves several enterprises distributed through several continents. Coordination of this project and management of distributed knowledge among the participants is performed through the Web. The tools developped in the project are used for keeping a memory of the project.
A distributed CM can be made of distributed, heterogeneous knowledge bases or of distributed, heterogeneous case bases, or of a multi-agent system. For example, in the MEMOLAB project, the CM of a research laboratory is implemented through a multi-agent system (with agents such as a bibliographic agent, a notebook agent, a "tips and tricks "agent and a proxy agent) (Vandenberghe and de Azevedo, 1995). The implementation of a distributed memory can also rely on both distributed case libraries and artificial agents responsible for information retrieval among such libraries (Nagendra Prasad and Plaza, 1996).
The construction of a distributed CM may often involve several experts. A protocol for collective knowledge elicitation is proposed in (Dieng, Giboin, Amergé, Corby, Després, Alpay, Labidi, Lapalut, 1996). Problems of consistency of the obtained CM elements, of cohabitation of several viewpoints must be solved: a protocol for cooperative creation of a consensual CM is thus offered in (Euzenat, 1996). In the particular case of a distributed CM relying on the reuse of ontologies, research on the collaborative creation of ontologies via ontology servers such as Ontolingua (Farquhar, Fikes and Rice, 1996), APECKS (Tennison and Shadboldt, 1998) or WebOnto (Domingue, 1998) can be exploited.
2.2.6 Combination of Several Techniques
In some cases, both informal knowledge (such as documents) and formal
knowledge (such as knowledge explicitly represented in a knowledge base)
are needed. Therefore research on the management of links between
document and knowledge base can be exploited (Martin
and Alpay, 1996; Euzenat, 1996).
By the same way, research on the semi-automatic extraction of knowledge
(for example, terminological knowledge, etc.) from documents thanks to
natural language analysis can be useful (Trigano,
1994).
(Kühn and Abecker, 1997) proposes
an interesting CM architecture where the CM can be composed of different
sorts of memories: documents, knowledge bases, etc.
2.3 Diffusion and Use of the Corporate Memory
2.3.1 Possible Modes of Diffusion
Adequate elements of the CM must be distributed to the adequate
members of the enterprise: this distribution may be passive or active,
as either the user can search by himself needed information where it is
available, or knowledge distribution can be systematically decided and
taken in charge by an adequate person or service of the enterprise. When
the company workers are too busy to look for relevant corporate information,
a passive distribution is insufficient: (Kuhn
and Abecker, 1997) recommends an active distribution (e.g. regular
recall of the existence of relevant information).
(Van Heijst, Van der Spek, and
Kruizinga, 1996) distinguishes several cases according to the kind
of collection and of diffusion of the CM :
Individuals and organizations can take advantage of the remarkable possibilities of access to data, to information and to knowledge provided by Internet. Knowledge diffusion can for example exploit the possible access to Internet or to an Intranet inside the enterprise. However, sometimes some reticences are expressed by the managers of some enterprises w.r.t. Internet and the Web, due to potential problems such as confidentiality, security, reliability of accessed information, risk of information excess that may disturb the employees in their work. But security problems are studied actively by researchers, as they are a significant condition for success of Internet-based applications such as electronic commerce.
Diffusion can rely on a knowledge server on the Web or on publication on the Web (Euzenat, 1996; Corby and Dieng, 1997). Different kinds of elements can be accessed through Internet/Intranet: documents (classic electronic documents, HTML documents...), databases, ontologies, knowledge bases, case bases, articles of electronic journals, etc. Therefore several kinds of knowledge servers can be thought out: document servers, ontology servers, knowledge base servers, database servers, journal servers or digital libraries. The main problems to be solved are retrieval of elements of the CM in answer to a request and adaptation of the answer to the user. Research on user profiling can thus be useful in this purpose (Sorensen, O'Riordan and O'Riordan, 1997).
Let us notice that a CM may not be restricted to the enterprise, but could include information and knowledge stemming from the external world but important for the enterprise work (cf. the so-called "economic intelligence"). Therefore, the retrieval and integration of such information explicitly put on the Web by other companies working in the same area may be interesting.
2.3.2.1. Example of Diffusion via Internet/Intranet
Let us detail an example of exploitation of Internet/Intranet. In our team, we have developped a component, called WebCokace, that enables to distribute expertise on the Internet (Corby and Dieng, 1997). The expertise is modelled in the CommonKADS framework (Breuker and Van de Velde, 1994) with the CML formalism (Schreiber, Wielinga, Akkermans, van de Velde, and Anjewierden, 1994). WebCokace relies on the hypothesis that CommonKADS may be useful for building knowledge-based corporate memories.
WebCokace takes advantage of the Web technology to interface an expertise model development environment with an HTTP server. The expertise model environment functions in a server mode and is connected to an HTTP server (that acts here as a client of the knowledge server) by means of a CGI interface. Modelled knowledge is then available on the Net.
In order to facilitate user interaction with the system, we have developped a search engine, a query language and an interpreter for this language. Users can emit queries to the knowledge server and get CommonKADS objects in response to the queries. CommonKADS objects are pretty-printed with HTML hypertext links to related objects in such a way that hypertext navigation is possible in expertise models. For example, a concept references its super types, a task its subtasks.
The system generates interactive graphic views on the expertise. It is possible to visualize concept and task hierarchies, domain models, etc. Clicking on a node of a hierarchy leads to the corresponding object definition. So the end-user may rely on the graphics instead of CML text.
The system also manages references between expertise models and electronic documents by means of HTML hypertext links and URL. A CommonKADS model can be annotated with references to source documents (e.g. technical documentation, articles, etc.), and conversely, a document can be annotated with references to expertise models. The links are activated once loaded in a Web browser and it is then possible to navigate between models and documents in a hypertext way.
Using WebCokace, we have developped a generic library for conflict solving in concurrent engineering, an oncology server and we have implemented parts of the CommonKADS modeling generic library.
WebCokace is implemented on the Centaur programming environment generator, developed in the Croap project at the INRIA. Thanks to the underlying generic technology (i.e. Centaur), WebCokace can be used as a program server for any programming language that is implemented in Centaur. Within Centaur, programs are internally manipulated as abstract syntax trees (AST). AST support abstract computations on programs that enable to answer to queries. This notion of program server can be useful in companies having libraries of programs to be included in their CM.
The CM is supposed to be used by adequate members of the enterprise: in all cases (documentary system, knowledge base, case-based system, Web-based system, etc), we must notice the importance of information search, if possible adapted to the users' needs, their activities and their work environment. The problems to be tackled are: How can the user express his/her requests? How to improve hypertext navigation by the user? How to retrieve elements of the CM in answer to a request? Is full-text search sufficient? How to index the documents to retrieve? What additional information (such as enterprise models, knowledge models, user models) could help to filter the information to be retrieved? Are inference capabilities needed in this purpose? Research on ontology servers such as Ontolingua (Farquhar, Fikes and Rice, 1996), APECKS (Tennison and Shadboldt, 1998) or WebOnto (Domingue, 1998) could also be exploited, since a part of the CM can rely on an ontology. A CM infrastructure relying on techniques of information search on the Internet is proposed in (Huynh, Popkin and Stecker, 1994).
2.4
Evaluation and Evolution of the Corporate Memory
2.4.1 Evaluation
of the Corporate Memory
As noticed in (Ermine, 1996), operational projects of CM are necessarily consuming and expensive. Therefore an evaluation of such projects is important, from several viewpoints: economico-financial, socio-organizational and technical.
From an economico-financial viewpoint, one aim of the CM is to improve the enterprise competitiveness. As noticed in (Durstewitz, 1994), it can be measured by a gain between the success of the enterprise products or services, and its production (and maintenance) costs. There must be an evaluation of the gain obtained thanks to the introduction of a CM, generally aimed at enhancing productivity. Return on investment is important for justifying the interest of building a CM, from the viewpoint of the managers. But methods or tools are needed to assess the actual improvement due to the introduction of the CM: it may be an improvement in safety - cf. avoidance of past errors -, in quality and in performance.
From a socio-organizational viewpoint, the CM can aim at improving employees' work organization (thanks to information circulation improvement, etc.) and employees' satisfaction in their work. But the criteria for such an evaluation are often qualitative and hardly quantitative: they can rely on classical criteria used for evaluating user-centered tools such as easiness of use, easiness of information retrieval, adequation of retrieved information, confidence in such information, usability for the user's activity, etc. As noticed in (Kuhn and Abecker, 1997), users' feedback should be exploited for detecting possible deficiencies of the CM and suggest improvements of the CM.
From a technical viewpoint, the transfer of know-how inside the enterprise seems to be an evident benefit. But an effective transfer depends on an effective use of the CM and on its adaptation to such a knowledge transfer.
There may be some bias in the use of the CM. The introduction of a CM can imply changes in individual and collective work in the enterprise. Some reorganizations prescribed by the managers may not be accepted by the employees. For example, an official procedure for storing lessons or experiences linked to a given project may be prescribed by the company managers but not respected for reasons such as lack of time, lack of motivation, etc. Moreover, a CM may be used otherwise than planned. We found very few publications analyzing reactions of CM users: for example, in (Ballay and Poitou, 1996), a survey of satisfaction of DIADEME users is presented. It relied on a questionnaire on their use of automatic bibliography and hypertext links, their experience and satisfaction of the databases, their experience and satisfaction with the full-text document retrieval TOPIC included in DIADEME, their satisfaction with the workstation. The lesson of this survey was that even though DIADEME was aimed at being a collective knowledge management system, its users rather exploited the system as a set of different specific tools.
In (Kuhn and Abecker, 1997), three case studies are analyzed: KONUS for crankshaft design, RITA for Quality Assurance for Vehicle Components and PS-Advisor for bid preparation for oil production system. The authors noticed that all three systems failed to go beyond prototype stadium and be integrated in the company daily operational work. The reasons of such failures were: "costs of customer-tailored solutions with unpredictable return of investment, insufficient experiences with CM applications, poor integration into the conventional Information Technology landscape". As a lesson learnt from these case studies, they suggested crucial requirements for a CM (see above), they proposed a general CM architecture and a kind of methodological guide for development of a CM, insisting on requirement analysis, human factors, cost-benefit analysis, knowledge evolution and technical realization.
In conclusion, we must distinguish evaluation by users (with criteria based on users' satisfaction) and strategic evaluation by managers (with criteria based on return on investment). At present, there are too few effective operational CM, and companies need to stand back for evaluating them precisely.
2.4.2 Maintenance and Evolution of the Corporate Memory
For maintenance and evolution of the CM, it is necessary to take into account the results of the evaluation of what already exists. Problems linked to addition of new knowledge, removal or modification of obsolete knowledge, coherence problems underlying a cooperative extension of the CM, must be tackled. Some of such problems were already relevant during the construction of the CM. Likewise, both organizational problems and technical problems underly the possible evolution of the CM. In the construction as in the evolution of the CM, some problems may stem from conflicts between persons, reticences, lack of motivation, lack of time.
The techniques used to maintain and make evolve the CM also depend on the kind of CM: according to the case, addition, removal or modification will concern elements of a knowledge base or cases in a case base or (elements of) documents in a document base or agents in a multi-agent system. The CM evolution also depends on whether the collection (resp. diffusion) of CM elements is passive or active (Van Heijst, Van der Spek, and Kruizinga, 1996). Evolution of the CM depends on both the CM builders/maintainers and the CM users.
According to (Kuhn and Abecker, 1997),
knowledge evolution should be "a continuous activity performed by a CM
administrator in close cooperation with the users who can make improvement
/ update suggestions tightly integrated into their work process". This
solution corresponds to an active collection and diffusion, as for instance
in the ICARE project (Bologna and Gameiro Pais,
1997). In some cases, a given service or a given person of the enterprise
is responsible for the maintenance/evolution of the CM. In other cases,
any employee may make evolve the CM, while respecting some constraints.
3 - EXAMPLES OF DEDICATED METHODS
This section will give few examples of methods dedicated to the building of a CM. The purpose of this description is to show the principles guiding some CM-dedicated methods (in comparison to knowledge engineering methods such as KREST or CommonKADS).
CYGMA (CYcle de vie et Gestion des Métiers et des Applications) is a method allowing the construction of a profession memory in a manufacturing industry (Bourne, 1997). It defines six categories of industrial knowledge for design activity:
REX method (Malvache and Prieur, 1993)
relies on the following steps: (1) analyse needs and identify sources of
experience, (2) construct elementary pieces of experience from documents,
databases or interviews, (3) build up a computer representation of the
knowledge domain, (4) install a software package on the user's workstation:
this package includes a multimedia interface and a retrieval engine
that produces information files on the basis of questions in natural language.
3.3 Method MKSM (CEA)
MKSM (Method for Knowledge System Management) (Ermine, 1996; Ermine, Chaillot, Bigeon, Charreton, Malavieille, 1996) aims at reducing complexity of knowledge system management, using different models at different grain levels. It is a systemic-based decision support method. It relies on the hypothesis that the knowledge assets of an organization can be considered as a complex system. Modelling such a complex system relies on several viewpoints: syntax, semantic and pragmatic, each viewpoint being itself modelled through three viewpoints: structure, function and evolution. The three components of a knowledge sytem are information (requiring data processing), signification (requiring task modelling) and context (requiring activity modelling). The method offers five modelling phases: knowledge system modelling, domain modelling, activity modelling, concept modelling, task modelling.
CYGMA is dedicated to profession memory, in the framework of a design task, while REX and MKSM do not focus on a kind of CM and do not restrict to a kind of task. REX relies on the building of pieces of experience, stemming from several kinds of sources (human, documents, databases); such pieces can be retrieved in answer to natural language request. MKSM takes inspiration of complex system theory for offering a theoretical analysis of an organization knowledge, considered as a complex system. MKSM proposed modelling phases are close to CommonKADS notions. All three methods were applied to several industrial applications. Criteria for comparing them more precisely could be: the complexity level of the method application, the kind of CM it enables to build, the kind of task it restricts to, the number and features of effective applications built with them, and evaluation of such applications by their end-users.
We presented a preliminary survey that needs to be completed and deepened in order to offer a methodological guide for the choice between the multiple methods and tools proposed. We can however propose some conclusions from this survey.
In all the described research, an important aspect is that an enterprise can be analyzed at several levels, according to several viewpoints. Most methods focused on some viewpoints and relied on an implicit or explicit model of the enterprise, or at least of the knowledge of the enterprise. The analysis of the enterprise needs for a CM can help determine the kind of needed CM. According to the case, it may imply to build an individual memory (cf. an expert retires or is muted, so it is interesting to make explicit, model and store this expert's know-how in a knowledge base or to store his experiences in a case base), a project memory (cf. elements of a given project could be necessary for later projects), a managerial memory needed by the company managers for strategic decisions, etc.
As a conclusion, the choice between the different construction techniques is based on several questions that an enterprise should answer before building a CM:
Ballay, J.-F. (1997). Capitaliser et transmettre les savoir-faire de l'entreprise, Eyrolles.
Ballay, J.-F., and Poitou J. P. (1996). Diadème : a Collective Knowledge Management System. In J. F. Schreinemakers ed, Knowledge Management: Organization, Competence and Methodology, Proc. of the 4th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'96), Rotterdam, the Netherlands, Wurzburg:Ergon, Advances in Knowledge Management, vol. 1, October 21-22, p. 265-285.
Bannon, L. J. and Kuutti, K. (1996). Shifting perspectives on organizational memory: from storage to active remembering. In Y. Wærn (1996)
Barthès, J.-P. (1996), ISMICK and Knowledge Management, In Advances in Knowledge Management: Organization Competence and Methodology, Volume 1, Ed. Jos F. Schreinemakers, p. 9-13.
Beauchène, D., Mahé, S., Rieu, C. (1996). Enterprise Know-How: Capitalization and Benchmarking with an Enterprise Organizational Model. In J. F. Schreinemakers ed, Knowledge Management: Organization, Competence and Methodology, Proc. of the 4th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'96), Rotterdam, the Netherlands, Wurzburg:Ergon, Advances in Knowledge Management, vol. 1, October 21-22, p. 194-206.
Bollon, T. (1997). Capitalisation des connaissances et conception: éléments de méthodologie. In J.-M. Fouet (Coord.), Connaissances et savoir-faire en entreprise: information et capitalisation, Paris, Hermès, pp. 130-153.
Bologna , G., and Gameiro Pais, J. (1997). ICARE: an operational knowledge management system. Proc. of the 5th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'97), Compiègne, France, p. 150-162.
Bourne, C. (1997). Catégorisation et formalisation des connaissances industrielles. In Connaissances et Savoir-faire en entreprise, ed. Hermes, p 179-197.
Breuker, J. and Van de Velde, W., eds (1994). CommonKADS Library for Expertise Modelling, Reusable Problem Solving Components. IOS Press, Amsterdam.
Buckingham Shum, S. (1997). Negotiating the construction and reconstruction of organisational memories. Journal of Universal Computer Science, 3(8), 899-928.
Corbel, J.C (1997). Méthodologie de retour d'experience: démarche MEREX de Renault. In Connaissances et Savoir-faire en entreprise, ed. Hermes, p 93-110.
Corby , O. , and Dieng R. (1996). Cokace: a Centaur-based environment for CommonKADS Conceptual Modelling Language. In W. Wahlster ed, Proc. of the 12th European Conference on Artificial Intelligence (ECAI'96), pp. 418-422, John Wiley & Sons, Ltd. Budapest, Hungary, 1996.
Corby , O. , and Dieng R. (1997). A CommonKADS Expertise Model Web Server. Proc. of the 5th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'97), Compiègne, France, p. 97-117. (WebCokace is available at the URL: http://www.inria.fr/acacia/Cokace)
Dieng, R., Giboin, A., Amergé, C., Corby, O., Després, S., Alpay, L., Labidi, S., Lapalut, S. (1996). Building of a Corporate Memory for Traffic Accident Analysis. Proceedings of the 10th Knowledge Acquisition for Knowledge-Based Systems Workshop (KAW'96), Banff, Canada, November, p. 35.1-35.20. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Domingue, J. (1998).Tadzebao and WebOnto: Discussing, Browsing, and Editing Ontologies on the Web, Accepted at the 11th Workshop on Knowledge Acquisition, Modeling and Management (KAW'98), April, 1998.
Durstewitz, M. (1994). Report on Workshop on Corporate Memory, Toulouse, http://www.delab.sintef.no/MNEMOS/external-info/cm-eurisko.txt
Eason, K. and Olphert, W. (1996). Early evaluation of the organisational implications of CSCW systems., in P. Thomas (Ed.) , CSCW Requirements and Evaluation, London: Springer, pp. 75-89.
Ermine, J. L. (1996) Les systèmes de connaissances. Hermès.
Ermine, J. L. , Chaillot, M., Bigeon, P., Charreton, B., Malavieille, D. (1996) . MKSM, a method for knowledge management. Proc. of the 5th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'97), Compiègne, France, p. 288 - 302.
Euzenat, J. (1996) . Corporate memory through cooperative creation of knowledge bases and hyper-documents. In B. Gaines, M. Musen eds, Proc of KAW'96, Banff, Canada, November, pp. 36-1 36-18. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Farquhar, A., Fikes, R. and Rice, J. (1996). The Ontolingua Server: a Tool for Collaborative Ontology Construction, USA. In B. Gaines, M. Musen eds, Proc of KAW'96, Banff, Canada, November 1996, pp. 44-1 44-19. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Feray, N. , Villefranche, L. (1997). Modèle des Données et de la Mémoire de l'Intranet MNEMOS, Technical Report, Laboratory PSI, Rouen.
Fox, M. S. (1993). Issues in Enterprise Modelling. In Systems Engineering in the Service of Humans, Proc. of the IEEE Conf. on Systems, Man and Cybernetics, p. 86-92, Le Touquet, France, October 17-20. Los Alamitos, CA : IEEE Computer Society.
Fraser, J. (1994). Managing Change through Enterprise Models, in Proc. of Expert Systems'94, the 14th Annual Conference of the British Computer Society Specialist Group on Expert Systems, Cambridge UK, December.
Gaines, B. R., Norrie D. H., Lapsley A. Z., Shaw M. L. G. (1996). Knowledge Management for Distributed Enterprises. In B. Gaines, M. Musen eds, Proc of KAW'96, Banff, Canada, November, pp. 37-1 37-18.
Grunstein (1995). La capitalisation des connaissances de l'entreprise, système de production de connaissances. L'entreprise apprenante et les Sciences de la Complexité. Aix-en-Provence, Mai.
Grunstein, M. and Barthès J.-P. (1996). An Industrial View of the Process of Capitalizing Knowledge, In J. F. Schreinemakers ed, Knowledge Management: Organization, Competence and Methodology, Proc. of the 4th Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'96), Rotterdam, the Netherlands, Ergon, October, p. 258-264.
Guérin, C. and Mahé, T. (1997). Entreprises, exercez votre mémoire! Sciences et Techniques, No 784.
Huynh M., Popkin L., Stecker M. (1994). Constructing a Corporate Memory Infrastructure from Internet Discovery Technology. White Papers, Marble Associates Inc., <http://www.marble.com/chi-bin/list-white-papers>.
Jones, S., Marsh, S. (1997). Human-Computer-Human Interaction: Trust in CSCW. SIGCHI Bulletin, 29(3), 36-40.
Karsenty, L. (1996). An empirical evaluation of design rationale documents, Electronic Proceedings of CHI'96 [http://www.acm.org/sigchi/chi96/proceedings/papers/Karsenty/lk_txt.htm]
Kingston, J. K. C. (1994). Modelling Business Processes using the Soft Systems Approach. In J. P. Barthès ed., Proc. of the 2nd Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'94), Compiègne, October 1994, pp. 149-159.
Knapp, E. (1997). Know-how's Not Easy: How to Keep knowledge management from flickering out. ComputerWorld, Leadership Series, 1/17/97.
Kühn O., Abecker A. (1997). Corporate Memories for Knowledge Management in Industrial Practice: Prospects and Challenges. Journal of Universal Computer Science, 3(8), 929-954.
Kurland, T. Barber, P. (1995). User requirements from a group perspective: the case of distance learning mediated by computer conferencing. In Peter Thomas (ed), CSCW Requirements and Evaluation, London: Springer, 57-74.
Loftus, E.L. (1997). Creating false memories. Scientific American, September 1997, 70-75.
Macaulay, L. (1996). Cooperation, Requirements Analysis and CSCW, in P. Thomas (Ed.) CSCW Requirements and Evaluation, pp. 39-55.
Macintosh, A. (1994). Corporate Knowledge Management State-of-the-Art Review. Proc. of the 2nd Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'94), Compiègne, France, pp. 131-145.
Macintosh, A. (1997). Knowledge asset management, AIring, (20), April 1997.
Malvache, P. and Prieur, P. (1993). Mastering corporate experience with the Rex method. In J. P. Barthès ed., Proc. of ISMICK'93, Compiègne, October, pp. 33-41.
Martin, Ph., and Alpay, L. (1996). Conceptual Structures and Structured Document. In Eklund, P. W. , Ellis, G., Mann, G. eds, Conceptual Structures: Knowledge Representation as Interlingua, ICCS'96, Springer-Verlag, LNAI 1115, pp. 145-159.
Morizet-Mahoudeaux, P. (1994). Basic Research Knowledge Management in Industry, Academia and Administration: A Japanese Perspective. Proc. of ISMICK'94, Compiègne, France, pp. 3-18.
Nagendra Prasad, M.V. N., Plaza, E. (1996), Corporate Memories as Distributed Case Libraries, Proc. of KAW'96, Banff, Alberta, Canada, November 9-14, p. 40-1 40-19. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Nonaka, I. (1991). The knowledge-creating company. Harvard Business Review. Nov-Dec., pp. 96-104.
O'Leary, D. E. (1997). The Internet, Intranets and the AI Renaissance. Computer, 30(1):71-78, Janvier.
Oliveira E. and Shmeil M. A. H. (1995). ARTOR - An Approach towards Artificial Organizations. Proc. of the 3rd Int. Symposium on the Management of Industrial and Corporate Knowledge (ISMICK'95), Compiègne, France, pp. 29-39.
Poitou, J.P. (1995). Documentation is Knowledge: An Anthropological Approach to Corporate Knowledge Management. Proc. of the 3rd Int. Symp. on the Management of Industrial and Corporate Knowledge (ISMICK'95), Compiègne, France, pp. 91-103.
Poitou, J.P. (1997). La Gestion Collective des Connaissances et la Mémoire individuelle, in Connaissances et Savoir-faire en entreprise, ed. Hermès, p 157-178.
Pomian (1996). Pomian, F. Mémoire d'entreprise, techniques et outils de la gestion du savoir. Ed Sapientia.
Schreiber, G., Wielinga, B., Akkermans, H. , van de Velde, W. and Anjewierden A. (1994). CML: The CommonKADS Conceptual Modelling Language. In L. Steels & al, eds, A Future for Knowledge Acquisition: Proc. of EKAW'94, pp. 125, Hoegaarden, Belgium, Sept. 1994. Springer-Verlag, LNAI n. 867.
Simon, G. (1996). Knowledge Acquisition and Modeling for Corporate Memory: Lessons learnt from Experience. In B. Gaines, M. Musen eds, Proc. of KAW'96, Banff, Canada, November, pp. 41-1 41-18. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Simon, G. (1997). Modèles et méthodes pour la conception des mémoires d'entreprise. Le système DOLMEN : une application en métallurgie. PhD Thesis, Université Henri Poincaré, Nancy I, Janvier.
Simon, G. and Grandbastien, M. (1995). Corporate knowledge: a case study in the detection of metallurgical flaws. Proc. of ISMICK'95, Compiègne, France, pp. 43-52.
Simone, C. (1996). Collective Memory from Everyday Work. In Y. Wærn (1996).
Sorensen H., O'Riordan, A. and O'Riordan, C. (1997). Profiling with the INFOrmer Text Filtering Agent, Journal of Universal Computer Science, 3(8), 988-1006.
Steels, L. (1993) Corporate knowledge management. Proc. of ISMICK'93, Compiègne, France, pp. 9-30.
Tennison J., and Shadbolt, N. R. (1998). APECKS: a Tool to Support Living Ontologies, Accepted at the 11th Workshop on Knowledge Acquisition, Modeling and Management (KAW'98), April, 1998.
Thomas, P. (1996). Introduction: CSCW Requirements and Evaluation. In P. Thomas (ed), CSCW Requirements and Evaluation, London: Springer, 1-9.
Tourtier, P.-A. (1995). Analyse préliminaire des métiers et de leurs interactions. Rapport intermédiaire du projet GENIE, INRIA-Dassault-Aviation.
Trigano, P. (1994). Automatic Indexation and Knowledge Storing. Proc. of ISMICK'94, Compiègne, France, pp. 223-235.
Urban, G.L. and E. von Hippel (1988). Lead user analyses for the development of new industrial products. Management Science, 1988. 34(5): p. 569-582. Also in http://iir1.uwaterloo.ca/MOTW96/readings96/urban_vonhippel.html
Uschold, M., King, M., Moralee, S. and Zorgios, Y. (1996). The Enterprise Ontology. March. http://www.aiai.ed.ac.uk/~entprise/enterprise/ontology.html
Van Engers, T. V., Mathies H., Leget J., and Dekker, C.C.C. (1995). Knowledge Management in the Dutch Tax and Customs Administration: Professionalisation within a Knowledge Intensive Organization. ISMICK'95, Compiègne, France, pp. 71-80.
Vandenberghe, L., and de Azevedo, H. (1995). Multi-Agent Systems & Knowlege Capitalisation: an Overview. Proc. of ISMICK'95, Compiègne, France, pp. 61-68.
Van der Spek R. (1994). Towards a methodology for knowledge management. In J. P. Barthès ed., Proc. of ISMICK'94, Compiègne, October 1994, pp. 93-102.
Van Heijst, G, Van der Spek, R., and Kruizinga, E. (1996). Organizing Corporate Memories. In B. Gaines, M. Musen eds, Proc. of KAW'96, Banff, Canada, November, pp. 42-1 42-17. Also in http://ksi.cpsc.ucalgary.ca/KAW/KAW96/KAW96Proc.html
Wærn, Y. (1996). Collective Learning and Collective Memory for Coping with Dynamic Complexity - Co-tech Workshop at ECSCW 95. SIGCHI Bulletin, 28(3),Also in http://www1.acm.org:82/sigs/sigchi/bulletin/1996.3/waern.html
Wisner, A. (1997). Anthropotechnologie: vers un monde industriel pluri-centrique. Toulouse: Octarès.